Cyber fraud case study: Failure to recognize phishing email
By Gracie Awalt, Marketing Associate
Texas Medical Liability Trust
A small, rural hospital contracted with an emergency medical group for emergency department coverage. The group was paid monthly by electronic funds transfer, or EFT, from the hospital’s account to the ED group’s account.
In June, the hospital received an email invoice from the ED group with instructions to send payment to a new account. The hospital sent the $200,500 payment to the new account on July 10.
On July 12, the payment was returned because the new account was frozen. On July 16, the ED group emailed new account information and instructions to the hospital. The hospital sent the $200,500 payment to the new account.
In early August, the ED group sent the next monthly invoice by email with instructions to send the funds to another new account. The hospital sent the $206,500 payment on August 13.
It was later discovered that the requests to send the funds to the new accounts were fraudulent. The ED group never sent the emails requesting EFT account changes. The cyber criminals who sent the fraudulent emails and set up the accounts ended up collecting $407,000 from the hospital.
When the hospital discovered that the money had been sent to an invalid account, the loss was reported to the hospital’s insurance agent and cyber liability carrier. The hospital was advised to take the following steps.
- File a complaint with the local police department.
- Submit a complaint to the FBI’s Internet Crime Complaint Center (IC3). Instructions are found at https://www.ic3.gov/default.aspx.
- Contact the bank’s fraud department to flag the transactions as fraudulent.
- Contact the local FBI office.
After the incident, the hospital began using the following fraud prevention measures.
- A change in policy that requires all wire transfer procedures to have oral confirmation from vendors and contractors if there are any changes in payment instructions.
- Managers are now required to send emails using two-step account verification procedures.
- Employees in the IT, Finance, and Revenue Cycle Departments attend required training on cyber security and cyber fraud risks.
Risk management considerations
Social engineering, or the “art of manipulating people in an online environment, encouraging them to divulge — in good faith — sensitive, personal information,” (1) typically involves a hacker using a compromised business email account to request money, passwords, banking information, or personally identifying information from the holder of the compromised account. The victim is deceived into thinking the request is from a legitimate source, such as a friend or a financial institution with whom the victim has a business relationship.
In this case, the hospital fell victim to a social engineering fraud through a phishing email. The compromised ED group email requested money through multiple wire transfers, tricking the hospital into sending $407,000.
The following practices can help combat phishing attacks.
- Be suspicious of emails from unknown sources, especially those requesting sensitive information or stressing the urgency and importance of the request.
- Train employees to recognize suspicious emails and forward them to someone who manages cyber security.
- Establish an incident response plan to initiate in case a phishing attack is successful.
- Use technology to detect and test emails for malicious content.
- Require multifactor authentication.
- Conduct regular security training for employees and provide testing to ensure understanding.
- Follow your instincts, and always report suspicious emails. (2)
Sources:
- Definition: Social engineering. Glossary. International Risk Management Institute. Available at https://www.irmi.com/term/insurance-definitions/social-engineering. Accessed September 16, 2019.
- Health industry cybersecurity practices. Healthcare & Public Health Sector Coordinating Councils. Department of Health and Human Services. Available at https://www.phe.gov/Preparedness/planning/405d/Documents/HICP-Main-508.pdf. Accessed September 16, 2019.
Gracie Awalt can be reached at gracie-awalt@tmlt.org.
Reprinted with permission from Texas Medical Liability Trust.
How to detect email fraud
By Sara Bergmanson, Digital and Social Media Specialist,
Texas Medical Liability Trust
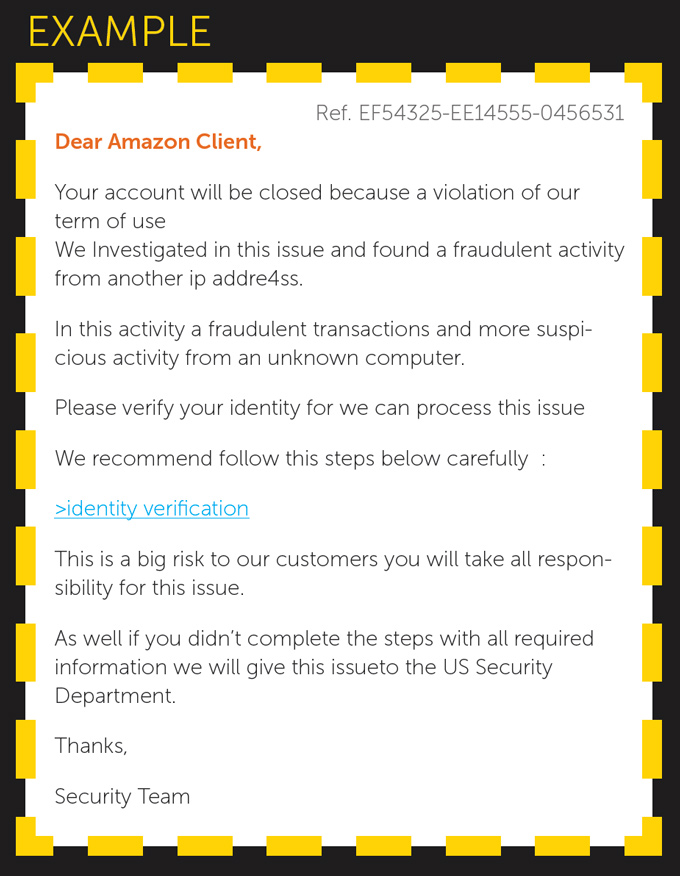
EMAIL PHISHING
Email fraud is also known as “phishing” or “spear phishing.”
Phishing — an attempt by cyber criminals using an email message that appears to come from a trustworthy source to get a recipient to provide sensitive or private information, such as a username, password, credit card number, or other secure data.
WHAT TO LOOK FOR:
SPELLING AND BAD GRAMMAR
- If you notice spelling or grammar mistakes in an email, it might be a scam — especially if the email appears to come from an organization you do business with. Legitimate businesses have communication departments or staff who review and edit email before sending it to customers.
- Check for proper spelling in web and email addresses. Cyber criminals use web and email domains that resemble the names of well-known companies but are slightly altered.
THREATS
- Email scams will entice you to respond to the message by threatening to close an account or by threatening another type of action. Legitimate institutions, particularly banks, do not typically communicate this way or ask you to click on a link in an email. Do not reply, click on links, or call phone numbers provided in the message.
- Contact the institution directly using contact information you know to be correct, if you have any doubts or questions.
- This also applies to emails with requests for urgent responses.
LINKS
- You can preview a link in an email message, without having to click on it, by hovering your cursor over the link. Either a small text box will appear with the full web address or it will appear in the lower left corner of your browser window.
- If the link appears suspicious or does not match the link in the message, do not click on it. These links can direct you to false websites or malicious software.
ASKING FOR PERSONAL INFORMATION
- If the email message is asking you to confirm or provide personal information, do not reply. Email is not a secure method for sharing sensitive information, and legitimate businesses do not ask you to send information this way.
SUSPICIOUS ATTACHMENTS
- Files attached in an email could contain viruses or other malware that can weaken your computer’s security. If you think you received a phishing email do not open or download any attachments.
When you’re unsure about the legitimacy of an email either call the sender or contact your security officer, IT staff, or consultant.
Sara Bergmanson can be reached at sara-bergmanson@tmlt.org.
Reprinted with permission from Texas Medical Liability Trust.